In this hyper-connected world of commerce, cloud computing is the next big innovation to lend that extra edge to any business. Today, most businesses opt for a cloud platform to streamline their computing process and avail on-demand resources without actually investing in the physical hardware. This requirement is fulfilled over the cloud or online via multiple sources where the businesses pay-as-they-go as per convenience.
If you already have a cloud computing solution in place, chances are that you are using AWS or Amazon Web Services. And, probable chances indicate that you’re looking to strengthen your cloud security and enable a robust cloud computing system in your company. As per the indications of Gartner, through 2022, 95% of security failures in the cloud will be due to the actions of the customer.
So, this is the scenario that we are looking to tackle presently. There are several areas of improvement in getting up a robust and secure Cloud Computing solution. As for AWS or Amazon Web Solutions, we have come up with certain tricks that will help you as a customer to safeguard your cloud assets and set up multiple layers of complex security.
Owned by Amazon Inc., AWS or Amazon Web Services is a cloud computing platform/ solution that provides on-demand cloud computing solutions to businesses and individuals across the globe on a pay-as-you-use basis. Today, it is one of the premier most cloud computing solutions out there and is acclaimed by users for its flexibility and cost-effectiveness. Subscribers and users hail its usage as a way of obtaining large scale computing capacity without making any investments in actual hardware or servers.
Amazon Web Services primarily offers two types of E2C storage volumes, also known as Elastic Block Storage or EBC. Amongst these two flavors, the standard volume is a novice as it transfers data at the same rate of a standard desktop drive while the flashier Provisioned volumes do the same at much faster rates with an output rate as high as 4000 IOPS (Input Output operations per second).
Now, the real problem arises in tracking the IOPS data in real-time as Amazon E2C doesn’t generally include tools or systems to do so. This has to be often accomplished with the use of third-party monitoring tools ensuring the surge of incoming data. This gets hastened often when you’re jumping several hoops thanks to the Provisioned volume.
You may also end up getting entangled with issues like the following:
The solution to this problem would be to look for alternative ways of tracking your IOPS.
Most organizations utilize numerous SaaS instruments to accomplish their business objectives on an everyday premise. With the logins and controls that shift over every one of them, it tends to be very testing to track consistently who is getting access to what information across the organization structure (even more concerning if the access is unauthorized). This is significant data since you need to be cautioned quickly if any of the movements are odd or malignant. The absence of a proper security strategy becomes even more visible when there is no security support in the implementation and management of these applications.
To accomplish better permeability on AWS, pursue these three accepted procedures:
Dive Deep: When it comes to comprehending what’s going on a host or remaining task at hand, you need more data than an IDS log can give. Exploring the intricacies of the process will help you to figure out your way through its mechanisms in a correct way. You have to know more than the way that a specific parcel went out over the wire. You ought to have the option to see explicit occasion’s additional time on explicit servers.
Look beyond Logs: Logs are fundamental, yet they frequently give just a thin perspective on what’s happening. It is one thing to see who is entering and leaving the structure, and very another to recognize what they are doing once they are inside. System based interruption discovery is restricted; have based interruption recognition gives you unquestionably more understanding.
Remember Insider Threats: If an occurrence happens, it is essential to see who caused it. Sadly, once in a while risk entertainers can be inward. This can originate from a misstep or from a malevolent aim. Notwithstanding the reason, some key markers that a risk originated from within are unordinary organized movements, unapproved introduces, anomalous login endeavors or disappointments, or key record changes. So, keep your gatekeeper up!
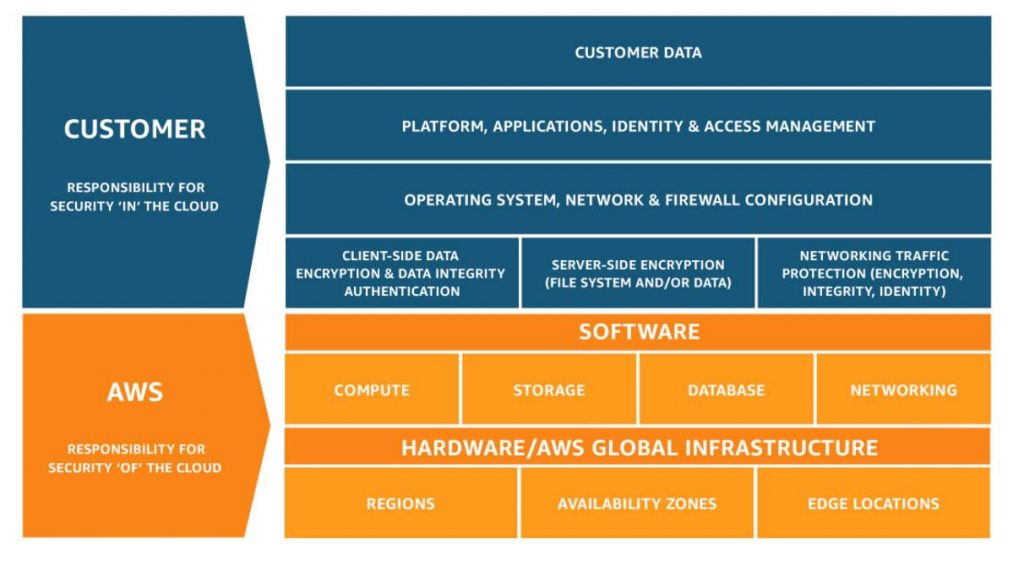
The above-mentioned image indicates the strict security responsibility divided between AWS and the customer. Hence, you as a customer, shoulder significant responsibility of setting up robust security to ensure the protection of your system. AWS offers numerous valuable security instruments and designs, however, it is essential to know where their duty closes and yours starts. In short:
We prescribe that you consider the security of your information on AWS even before you choose to relocate.
The obligation is a key theme in cloud security. At the point when a security episode happens, you have to realize who is mindful so you can make a suitable move.
Today, suppliers like AWS take on much increasingly aggregate security responsibility for everything over the virtual machine layer. Be that as it may, clients still need to assume liability for things like access control, checking, and review logging. By adopting a proactive strategy to characterizing access levels and observing movement over the system, organizations can be certain that if something goes wrong inside their AWS condition, they can pinpoint obligation with exactness.
Taking strict measures to curb the same would help you to not only protect your sensitive data but also complement your overall cloud security strategy. Tracking potential threats and loopholes will go a long way in ensuring a robust security process in place for your AWS needs.
Numerous organizations trust their sensitive information, similar to PHI, Mastercard information, and money related credentials, to cloud specialist co-ops like AWS. You can do this, yet you should remember the manners by which this makes you an objective for aggressors or potential online threats. The key is to comprehend what aggressors/ hackers or data thieves follow. Most security occurrences happen in light of accreditation robbery — not refined zero-day assaults against cloud suppliers themselves.
Certifications are a goldmine for assailants for one significant explanation: they are the keys to the realm, allowing access to an immense measure of information by misusing a solitary information source. You can preemptively secure your accreditations and information in various manners. We suggest that you:
In cloud computing, multi-tenancy generally indicated to more risk to data threats and online threats. However, in practice, it all revolves around the robustness of your infrastructure. This will lead to the complete improvement of your existing systems while simultaneously safeguarding it from potential threats.
While suppliers like AWS are very much aware of these worries and have executed layers of assurance to guarantee that you — and you — see your information, you can and should take various additional safety measures without anyone else. Trends show that there is a high risk involved in multi-tenancy and thus, you should put significant emphasis on getting it right.

On the off chance that your association is under obligation/ compliance to any consistency structures, you have to take a gander at how that will function in AWS. While cloud suppliers like AWS do furnish organizations with a specific degree of insurance, they just can’t cover each part of the problem.
AWS can (and does) offer assurances, for example, encryption of PII, both very still and in flight, yet it doesn’t constantly screen information for peculiar conduct, give have level bits of knowledge that can get to the base of the issue, etc. It isn’t constantly clear to figure out where AWS’s consistency highlights end and where another arrangement needs to become an integral factor to fill in the holes, yet it is basic to do the examination for your specific use case and ensure you don’t leave yourself uncovered.
Therefore, with the above-mentioned tricks and techniques, you will be able to create a solid cloud computing architecture and avoid leaving any security loopholes. It is also recommended that you consult an expert if you face problems regarding the implementation of these steps to ensure a smoother transition.
Stop, read and acquire deep insights into complex issues
© 2025 Copyright - JanBask.com | Designed by - JanBask Digital Design
Write a Comment